Following tech news can feel like living on the DMZ between a utopia and the apocalypse. We’re always one public scandal, earnings call, or product announcement away from tipping the scales in either direction. This year, both sides showed up in full force.

Source: Temple.edu
Andrew Bustamante recently responded to a question on a subreddit thread on Reddit which asked what the biggest threat to the America national security in the future will be. He replied saying blockchain technology will be the biggest threat and whoever manages to figure out the technology first wins.
The subreddit thread where the question was raised is a thread dedicated to Bustamante’s ‘Everyday Espionage’, where he supposedly teaches people to benefit from international espionage techniques by implementing them in daily lives. Considering the fact that Bustamante is reportedly a former CIA intelligence officer, U.S. Air Force veteran and Fortune 10 corporate advisor, he does have the qualifications to do so.
On 22 December 2018, the question was raised in the subreddit thread, together with several possible answers such as “climate change”, “Iran”, “North Korea” or “Russia”. He responded saying blockchain technology is “super powerful stuff”, and the whoever is capable of figuring out “how to hack it, manipulate it or bring it down wins”. However, he did not elaborate further on how exactly blockchain could threaten the country’s security.
Since then, multiple Redditors have speculated possible theories regarding Bustamante’s remarks on the technology. One of them suggested that the ability to create false data within the blockchain would be disastrous when paired with the high difficulty of fixing data in a blockchain-based system. Another Redditor suggested that blockchain offers the potential of making certain transactions “untraceable” and “anonymous”, thus ending up being a possible threat to security.
Quantum computing was also mentioned in the thread. Bustamante replied to a Redditor’s question asking for clarification whether developments in blockchain or quantum computing would be a more concerning factor to the country’s security. He replied that the Redditor had a “fair point”, and this remark a lot sparked new discussions on the topic.
As quantum computing was said to hold the possibility of permanently changing the cryptographic protection that defines blockchain, it was speculated that quantum computing was what Bustamante was referring to by his “bring it down” remark.
Over the past few months, the U.S. Department of Justice (DoJ) had charged several people from Russia’s Main Intelligence Directorate (GRU) for crypto-related crimes. In July, the DoJ charged twelve individuals while another seven officers were charged in October, all from the GRU and involved in crypto-related hacking operations.
Source: Cryptoverze
Foxbit co-founder Gustavo Schiavon, known affectively as Guto, has passed away in a car accident in the Brazilian state of São Paulo.
While driving between Marília city and São Paulo capital his car spun under heavy rain and got hit, back side first, by a large cargo truck. The automobile was reduced to a fraction of its size by the impact.
Guto was accompanied by his girlfriend Ariadny Rinolfi who survived the crash but is in serious condition under intensive care at a São Paulo hospital.
A second fatal victim was involved in a different automobile. A total of 2 passenger cars and 2 large trucks were involved in the crash.
Foxbit
Schiavon, who held a degree in Information Systems, founded Foxbit in 2014. The business quickly became Brazil’s largest Bitcoin exchange.
In March 2018 Foxbit was hacked and lost over R$ 1 million in funds. The company had enough reserves to cover the customers’ balances and avoid a Mt. Gox like scenario.
Four partners founded Foxbit: Schiavon, João Canhada, Marcos Henrique and Felipe Trovão.
The Foxbit team earned several prizes and recognition for their innovative work with cryptocurrencies in Brazil.
Also in 2018 Foxbit got involved in a landmark lawsuit against a bank which shut down their main account due to “concerns over money laundering security” although no evidence of any wrongdoing was presented in the case. The bank’s argument was that it had the right to close down accounts, at their sole discretion, which they felt could “pose risks”. The ruling became a negative precedent for cryptocurrency businesses in Brazil. Later in the year, Brazil’s second highest court used this lawsuit to decide that banks had the right to unilaterally close bank accounts.
Source: Crypto.Bi
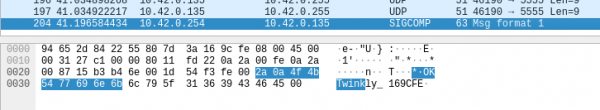
Researchers playing with Twinkly IoT lights found security weaknesses that allowed them to display custom lighting effects and to remotely turn off their Christmas brilliance. They estimate that about 20,000 devices are reachable over the internet.
The LEDs in Twinkly lights can be controlled individually. Exploiting inherent security weaknesses related to authentication and the communication of commands, the researchers were able to use the curtain of lights to play Snake, the game made so popular by Nokia phones in the late 1990s.
Users can manage their Twinkly smart decoration via a mobile app that sends unencrypted communication over the local network; this makes trivial analyzing the traffic from a man-in-the-middle position.
To talk to the lights, the app discovers them by running a UDP broadcast to port 5555 and receives in return an IP address and the name of the device.
“Once the application knows the IP address of the lights, it authenticates with them, receives an authentication token and retrieves information about the device. The authentication process, although a good idea, is flawed,” said the researchers from MWR InfoSecurity, a company recently acquired by F-Secure.
After analyzing the hardware internals and the mobile app, the researchers had a clear view of how the entire communication and authentication process worked.
They found the calls to the API endpoints, the algorithms used for creating the authentication challenge-responses.
Another discovery relates to the firmware update process, which does not use signatures to check the authenticity of the files received; this allows installing an arbitrary firmware “to the device over the local network without any real authentication or authorization, making it straightforward to gain arbitrary code execution.”
Hardcoded in the firmware is a username/password, used to connect to a private broker through the Message Queuing Telemetry Transport (MQTT) protocol for exchanging messages with remote IoT boards and sensors.
Seeking Reduced Risk?
See how Strategic Beta ETFs can help manage risk and seek to improve outcomes.
The MQTT protocol is not complex and it follows the publish/subscribe communication model, where the source and recipient of the message are oblivious of each other; when a publisher sends a message, it is received by all subscribers to that topic or class.
MQTT allows subscribing to a topic using wildcards using the symbol ‘#’ and doing so to the root means access to all topics and, implicitly, the information published by the lights.
“Monitoring the root for unique mac addresses we estimate there are almost 20,000 devices out there,” MWR Labs says.

Remote tampering with the lights is not difficult
Considering these security faults, it would be easy for an attacker on the network to intercept the communication between the Twinkly lights and the mobile app and use them to manipulate the LEDs into custom patterns or turn them off.
“As any MQTT node can publish to any topic, it is thus possible for anyone to issue commands to any set of lights and turn them off. We tested this remotely from AWS against the lights in the office and it worked perfectly,” MWR Labs experts note in a technical blog post.
To demonstrate remote management of the Twinkly lights across the world, the researchers turned to the DNS rebinding attack technique, known in the infosec industry for over a decade.
An attacker can use DNS rebinding to bypass the same-origin policy (SOP) in web browsers and turn them into a proxy for communicating with devices on the network. All the user would have to do for this to happen is access the wrong link.
MWR Labs created a malicious website specifically for this purpose. When the victim loads it, all the devices on the local network are enumerated. If Twinkly lights are available, they will be configured to show the message ‘Hack the Planet!’ as you can see in the video below.
The vulnerabilities found in Twinkly lights are the exact opposite for the IoT space. In this case, there is little damage an attacker can do by hacking the lights, but other targets may be more valuable, the researchers say.
Source: Bleeping Computer
A possible compromise of servers where NASA stored data on current and former employees may have given hackers access to social security numbers (SSN) and personally identifiable information (PII).
The incident occurred on or before October 23, when NASA cybersecurity team started to look into a possible server breach. Immediate action secured the machines and the data they stored.
Gatwick Airport, the UK’s second largest airport, has just become a key example of how thoroughly today’s consumer tech can disrupt our infrastructure. The airport briefly suspended all flights again Friday, the third time in three days, due to suspected drone sightings in the area. That’s right — drones were able to shut down a major UK artery for well over 24 hours, as police and armed forces have seemingly been unable to find those responsible.
Crypto markets are seeing their fifth day of green, with virtually all of the top 20 cryptocurrencies showing a strong burst of growth, as data from Coin360 shows.
Major cryptocurrency exchange and wallet Coinbase recently made what it claims is the largest transfer of crypto on record, a company blog post reports Dec. 19.
According to the post, 5 percent of all Bitcoin (BTC), 8 percent of all Ethereum (ETH), and 25 percent of all Litecoin (LTC), along with “many other assets” were moved to new cold storage infrastructure in what the firm “believe[s] is the largest crypto migration on record.”
On Tuesday, Apple unveiled its list of the most downloaded iPhone apps of 2018. Topping the list is YouTube, followed by Instagram, Snapchat, Messenger and Facebook, respectively.
Bitmoji — a Snapchat-owned app that lets users create an emoji that looks like them — dropped to sixth place on the list. It was the most downloaded app last year.
It’s been a challenging year for some social media companies, such as Facebook, which has faced criticism over privacy issues, data misuse, misinformation and election meddling on its platform. Nevertheless, Facebook’s flagship app and two others owned by the company (Instagram and Messenger) made the top five on the most downloaded list.
Snapchat also faced challenges this year, including navigating a controversial redesign that was widely panned by users, and heightened competition from Instagram — which has copied many of its popular features.
Once again, the most popular paid app was selfie-editing tool Facetune ($3.99). Kirakira+ ($0.99), which lets you add cool effects to videos and photos, took second place.
Apple declined to say how many times the apps have been downloaded.
In gaming, it was no surprise that the immensely popular Fortnite topped the charts. The number two spot went to Helix Jump, a game in which players navigate a falling ball through a maze. That was followed by Rise Up, a game that lets players protect a balloon from obstacles.
Source: CNN