Ransomware Hostage Rescue Manual
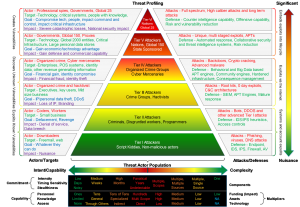
Ransomware can take different forms, but in its essence, it denies access to a device or files until a ransom has been paid.
In this manual, we discuss ransomware as PC or Mac-based malicious software that encrypts a user or company’s files and forces them to pay a fee to the hacker in order to regain access to their own files.
The hackers primarily use the following vectors to infect a machine: phishing emails, unpatched programs, compromised websites, poisoned online advertising, and free software downloads.
Download full document addressing Ransomeware Hostage today.
[embeddoc url=”https://itblogr.com/wp-content/uploads/2019/12/Ransomeware-Hostage-Rescue-Manual.pdf” viewer=”google”]