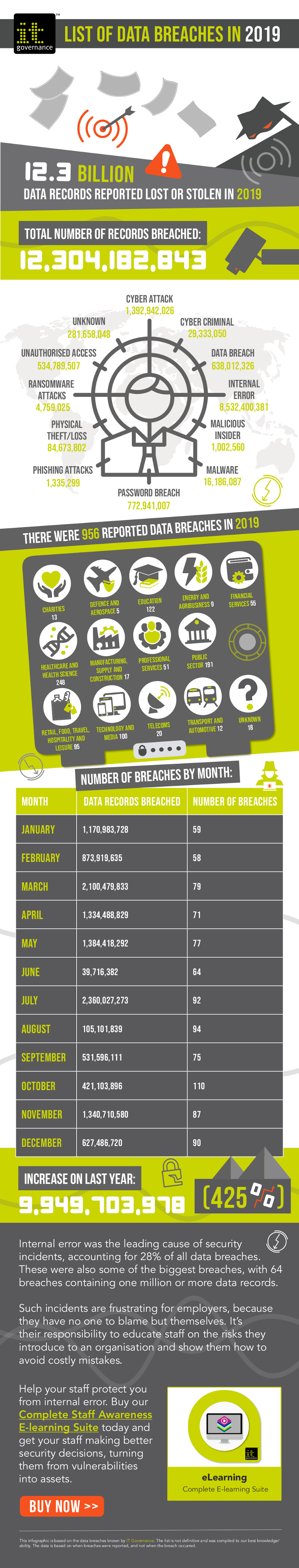
The new decade has begun relatively well, with a six-month low of only 61 disclosed cybersecurity incidents.
By comparison, 2019 saw an average of almost 80 data breaches and cyber attacks per month.
It’s not all good news, though. Several major incidents occurred in January, boosting the total number of breached records to a substantial 1,505,372,820.
That includes several worrying incidents involving UK organizations – which are highlighted in bold.
You can find detailed breakdowns of some of the more notable incidents by subscribing to our Round-ups or by visiting our cheatsheet page where we have a dedicated variety of handy cybersecurity cheatsheets.
In the meantime, you can check out the full list here:
Cyber attacks
- Royal Yachting Association tells members to reset passwords after intrusion (unknown)
- Oregon’s Klamath County Veterans Service Office says it’s been breached (unknown)
- HappyHotel, Japanese short-time love hotel, hit by cyber criminals (unknown)
- Native American Rehabilitation Association of the Northwest reports Emotet attack (344)
- Albany Airport announces that a malware attack occurred on Christmas Day (unknown)
- Manor Independent School District, TX, loses $2.3M in phishing scam (unknown)
- Russian agents reportedly phished organisation at the centre of Trump impeachment scandal (unknown)
- The New Mexico Public Regulation Commission is investigating after state-sponsored hack (unknown)
- Adventist Health notifies patients of phishing incident (2,653)
- Chinese hackers blamed as Mitsubishi Electric discloses data breach (unknown)
- Greece says no data stolen in Turkish hacker attacks on state bodies (0)
- Detroit suffers data breach affecting city workers and residents (unknown)
- SuperCasino breached, with users’ personal info stolen (unknown)
- VillageCareMAX members data nabbed in BEC scheme (unknown)
Ransomware
- Travelex suspends services after ransomware attack (unknown)
- Richmond County Schools, MI, refuses to pay $10k ransom (unknown)
- Saskatchewan’s eHealth records held hostage by cyber criminals (unknown)
- Bartlett Public Library District, IL, computers disabled by ransomware (unknown)
- Enloe Medical Center rescheduled elective procedures after being shut out of its systems (unknown)
- Anchorage-based bty Dental notifies patients after ransomware attack (2,008)
- Patients at The Center for Facial Restoration receive ransom demand (unknown)
- Dawson’s Creek, British Columbia, hit by ransomware (unknown)
- California’s Panama-Vista School District says ransomware will delay report cards (15,985)
- Colonie, NY, working on backups after cyber criminals lock down computer system (unknown)
- New Jersey synagogue hit by Sodinokibi ransomware (unknown)
- Oman’s largest insurance company shut down by ransomware (unknown)
Data breaches
- Data leak exposes the owners of thousands of anonymous offshore companies (unknown)
- Fresh Film Productions leaks personal data of Dove ‘real people’ ad participants (1,500)
- Insecure database leaks Brits’ passport info online (+2,000)
- Consultancy firms leak data on workers (+2,000)
- UK betting firms given vast access to children’s personal data (28 million)
- University of Ottawa says password-protected laptop was stolen from campus (188)
- IT provider for Fayette Co., OH, loses six months of data in mix-up (unknown)
- Database belonging to people-finder site CheckPeople.com found online (56.25 million)
- Software provider Front Rush exposed server of student’s information (700,000)
- Every day, millions of patients’ health records are spilled onto the Internet (1.19 billion)
- Peekaboo Moments app left baby videos and users’ email address exposed online (800,000)
- Smart city system City Brain exposed its data online – again (unknown)
- A hacker is selling personal data that they claim belongs to San Fran-based LimeLeads (49 million)
- Amazon Web Services bucket containing webcam models’ data leaked online (875,000)
- Investigation underway into privacy breach at City of Corner Brook’s website (unknown)
- Ukraine says personal data leaked from government jobs portal (unknown)
- Hacker leaks database of passwords for home routers and smart devices (515,000)
- Microsoft discloses security breach of customer support system (250 million)
- PIH Health notifies patients of data breach after email gaffe (200,000)
- Iowa Department of Human Services discloses janitorial mishap involving personal data (4,784)
- H&M under investigation amid claims of massive privacy breach (unknown)
Financial information
- The City of Bend, OR, discloses Click2Gov breach (unknown)
- Australia’s P&N Bank tells customers that account info and balanced were exposed (unknown)
- Texas-based RealPage down $10.5M after hackers break into finance systems (unknown)
- South Carolina’s Greenville Water targeted by cyber criminals (unknown)
Malicious insiders and miscellaneous incidents
- Air China suspends flight attendant who shared celebrities’ info online (20)
- University Hospital Limerick investigating staff who allegedly leaked patient info (unknown)
- Amazon fires several employees who shared customers’ info with a third party (unknown)
- Mercy Health Lorain Hospital Laboratory says printer error caused data breach (unknown)
- Amazon-owned Ring fired employees for improperly accessing users’ videos (unknown)
- Four Hyderabad men arrested for stealing sensitive information from a pharmaceutical firm (unknown)
- Cardiovascular Associates of Arizona reports office burglary (unknown)
- Break-in at the Hospice of Anchorage could mean breach of patient data (unknown)
- Laptop stolen from Saskatoon Sexual Health in 2018 contained sensitive patient data (156)
- Detroit-based Beaumont Health investigating after employee accessed patient files (1,182)
In other news…
- Dixons Carphone fined £500,000 for data breach that affected 14 million people
- National Lottery hacker jailed for nine months
- Five-year sentence for hackers who targeted 700 bank and mobile phone accounts
- Louis man jailed for using data breach info leaks to claim $12M in tax refunds
- Singapore’s public healthcare cluster NHG fines $6,000 for failing to secure personal data
- Sodinokibi ransomware publishes stolen data after victims fail to pay up in time
- Vietnam government drafts decree to protect personal data
- Brazilian prosecutors charge US journalist and activist with cyber crimes
Source: IT Governance