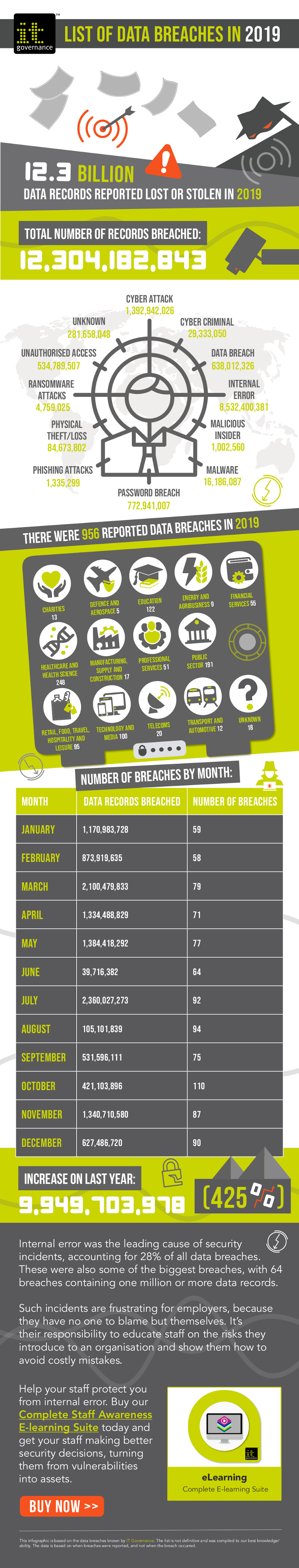
Throughout the year 2019, we kept an eye on cyber attack and data breach reported in mainstream publications, releasing our findings in our monthly blog series.
This allowed us to see how many security incidents were occurring, how many records were involved and which industries were worst affected.
Did you know, for example, that July was the worst month of the year in terms of breached records? Or that the leading cause of data breaches was internal error?
With 2019 in the books, we’ve summarised these and other facts in infographics below
Source: IT Governance



