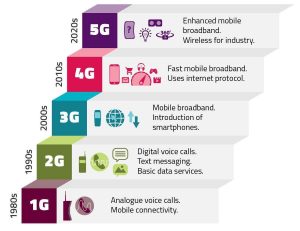
Source: 5G exposed

Source: 5G exposed
Amazon.com Inc. is developing a voice-activated wearable device that can recognize human emotions.
The wrist-worn gadget is described as a health and wellness product in internal documents reviewed by Bloomberg. It’s a collaboration between Lab126, the hardware development group behind Amazon’s Fire phone and Echo smart speaker, and the Alexa voice software team.
Designed to work with a smartphone app, the device has microphones paired with software that can discern the wearer’s emotional state from the sound of his or her voice, according to the documents and a person familiar with the program. Eventually the technology could be able to advise the wearer how to interact more effectively with others, the documents show.
It’s unclear how far along the project is, or if it will ever become a commercial device. Amazon gives teams wide latitude to experiment with products, some of which will never come to market. Work on the project, code-named Dylan, was ongoing recently, according to the documents and the person, who requested anonymity to discuss an internal matter. A beta testing program is underway, this person said, though it’s unclear whether the trial includes prototype hardware, the emotion-detecting software or both. Amazon declined to comment.
The notion of building machines that can understand human emotions has long been a staple of science fiction, from stories by Isaac Asimov to Star Trek’s android Data. Amid advances in machine learning and voice and image recognition, the concept has recently marched toward reality. Companies including Microsoft Corp., Alphabet Inc.’s Google and IBM Corp., among a host of other firms, are developing technologies designed to derive emotional states from images, audio data and other inputs. Amazon has discussed publicly its desire to build a more lifelike voice assistant.
The technology could help the company gain insights for potential health products or be used to better target advertising or product recommendations. The concept is likely to add fuel to the debate about the amount and type of personal data scooped up by technology giants, which already collect reams of information about their customers. Earlier this year, Bloomberg reported that Amazon has a team listening to and annotating audio clips captured by the company’s Echo line of voice-activated speakers.
A U.S. patent filed in 2017 describes a system in which voice software uses analysis of vocal patterns to determine how a user is feeling, discerning among “joy, anger, sorrow, sadness, fear, disgust, boredom, stress, or other emotional states.” The patent, made public last year, suggests Amazon could use knowledge of a user’s emotions to recommend products or otherwise tailor responses.
A diagram in the patent filing says the technology can detect an abnormal emotional condition and shows a sniffling woman telling Alexa she’s hungry. The digital assistant, picking up that she has a cold, asks the woman if she would like a recipe for chicken soup.
A second patent awarded to Amazon mentions a system that uses techniques to distinguish the wearer’s speech from background noises. Amazon documents reviewed by Bloomberg say the wearable device will take advantage of such technology.
Amazon’s work on a wearable device underscores its ambitions of becoming a leading maker of both cutting-edge speech recognition software and consumer electronics. The Echo smart speaker line and embedded Alexa voice software have popularized the use of voice commands in the home. The company has also added voice control to Fire-branded video streaming devices for television, as well as tablets.
But Amazon’s efforts to create smartphone software to rival Apple Inc. or Google have failed. So the company is trying to make Alexa ubiquitous in other ways. Bloomberg reported earlier this year that Amazon was developing wireless earbuds, similar to Apple AirPods, that are expected to include the Alexa voice software. The company has begun distributing Echo Auto, a dashboard-mounted speaker and microphone array designed to pair with a smartphone, and says it received 1 million pre-orders.
Amazon has also been working on a domestic robot, Bloomberg reported last year. Codenamed “Vesta,” after the Roman goddess of the hearth, home and family, the bot could be a kind of mobile Alexa, according to people familiar with the project. Prototypes of the robot can navigate through homes like a self-driving car.
Source: Bloomberg

Born2Root: 2: Vulnhub Walkthrough
SP ike: Vulnhub Lab Walkthrough
Hack the Box : Irked Walkthrough
Hack the Box: Teacher Walkthrough
SP eric: Vulnhub Lab Walkthrough
Hack the Box Vault: Walkthrough
OverTheWire – Natas Walkthrough (0-11)
Hack the Box Curling: Walkthrough
Hack the Box Frolic: Walkthrough
Hack the Box Carrier: Walkthrough
Web Developer: 1: Vulnhub Lab Walkthrough
HackInOS:1: Vulnhub Lab Walkthrough
unknowndevice64: 1: Vulnhub Lab Walkthrough
Casino Royale: 1 Vulnhub Walkthrough
Replay: 1: Vulnhub Lab Walkthrough
Hack the Box Access: Walkthrough
W34kn3ss 1: Vulnhub Lab Walkthrough
Matrix 2: Vulnhub Lab Walkthrough
Vulnhub: RootThis: 1 Walkthrough
Hack the Box Zipper: Walkthrough
Hack the Box: Giddy Walkthrough
Hack the Box: Ypuffy Walkthrough
Hack the Box: SecNotes Walkthrough
Hack the Box: Fighter Walkthrough
Hack the Box: Mischief Walkthrough
Hack the Box: Nightmare Walkthrough
Hack the Box: Waldo Walkthrough
Hack the Box: Active Walkthrough
Moonraker:1 Vulnhub Walkthrough
Hack the Box: Hawk Walkthrough
Typhoon: 1.02 Vulnhub Walkthrough
Hack the Box: TartarSauce Walkthrough
FourAndSix: 2 Vulnhub Walkthrough
Fowsniff: 1 Vulnhub Walkthrough
Hack the Box: Jerry Walkthrough
Hack the Raven: Walkthrough (CTF Challenge)
Hack the Box: Dropzone Walkthrough
Hack the Box: Bounty Walkthrough
Hack the Box: DevOops Walkthrough
Hack the Box: Olympus Walkthrough
Hack the Box: Sunday Walkthrough
Hack the Gemini inc:2 (CTF Challenge)
Hack the Box Challenge: Canape Walkthrough
Hack the MinU: 1 (CTF Challenge)
Hack the ROP Primer: 1.0.1 (CTF Challenge)
Hack the Box: Fulcrum Walkthrough
Hack the Box: Poison Walkthrough
Hack the /dev/random: K2 VM (boot2root Challenge)
Hack the Box: Stratosphere Walkthrough
Hack the Box: Celestial Walkthrough
Hack the Android4: Walkthrough (CTF Challenge)
Hack the Box: Minion Walkthrough
Hack the ch4inrulz: 1.0.1 (CTF Challenge)
Hack the Wakanda: 1 (CTF Challenge)
Hack the WinterMute: 1 (CTF Challenge)
Hack the Box: Holiday Walkthrough
Hack the Box: Silo Walkthrough
Hack the Lampião: 1 (CTF Challenge)
Hack the Bulldog:2 (CTF Challenge)
Overthewire – Bandit Walkthrough (21-34)
Hack the Box: Bart Walkthrough
Hack the Box: Valentine Walkthrough
Hack the Box: Aragog Walkthrough
Hack the Jarbas: 1 (CTF Challenge)
OverTheWire – Bandit Walkthrough (14-21)
Hack the Temple of Doom (CTF Challenge)
Hack the Golden Eye:1 (CTF Challenge)
Hack the FourAndSix (CTF Challenge)
Hack the Blacklight: 1 (CTF Challenge)
Hack the Basic Pentesting:2 VM (CTF Challenge)
Hack the Billu Box2 VM (Boot to Root)
Hack the Lin.Security VM (Boot to Root)
Hack The Toppo:1 VM (CTF Challenge)
Hack the Box Challenge: Ariekei Walkthrough
Hack the Violator (CTF Challenge)
OverTheWire – Bandit Walkthrough (1-14)
Hack the Teuchter VM (CTF Challenge)
Hack the Box Challenge: Enterprises Walkthrough
Hack the Box Challenge: Falafel Walkthrough
Hack the Box Challenge: Charon Walkthrough
Hack the PinkyPalace VM (CTF Challenge)
Hack the Box Challenge: Jail Walkthrough
Hack the Box Challenge: Nibble Walkthrough
Hack The Blackmarket VM (CTF Challenge)
Hack the Box: October Walkthrough
Hack The Box : Nineveh Walkthrough
Hack The Gemini Inc (CTF Challenge)
Hack The Vulnhub Pentester Lab: S2-052
Hack the Box Challenge: Sneaky Walkthrough
Hack the Box Challenge: Chatterbox Walkthrough
Hack the Box Challenge: Crimestoppers Walkthrough
Hack the Box Challenge: Jeeves Walkthrough
Hack the Trollcave VM (Boot to Root)
Hack the Box Challenge: Fluxcapacitor Walkthrough
Hack the Box Challenge: Tally Walkthrough
Hack the Box Challenge: Inception Walkthrough
Hack the Box Challenge Bashed Walkthrough
Hack the Box Challenge Kotarak Walkthrough
Hack the Box Challenge Lazy Walkthrough
Hack the Box Challenge: Optimum Walkthrough
Hack the Box Challenge: Brainfuck Walkthrough
Hack the Box Challenge: Europa Walkthrough
Hack the Box Challenge: Calamity Walkthrough
Hack the Box Challenge: Shrek Walkthrough
Hack the Box Challenge: Bank Walkthrough
Hack the BSides Vancouver:2018 VM (Boot2Root Challenge)
Hack the Box Challenge: Mantis Walkthrough
Hack the Box Challenge: Shocker Walkthrough
Hack the Box Challenge: Devel Walkthrough
Hack the Box Challenge: Granny Walkthrough
Hack the Box Challenge: Node Walkthrough
Hack the Box Challenge: Haircut Walkthrough
Hack the Box Challenge: Arctic Walkthrough
Hack the Box Challenge: Tenten Walkthrough
Hack the Box Challenge: Joker Walkthrough
Hack the Box Challenge: Popcorn Walkthrough
Hack the Box Challenge: Cronos Walkthrough
Hack the Box Challenge: Beep Walkthrough
Hack the Bob: 1.0.1 VM (CTF Challenge)
Hack the Box Challenge: Legacy Walkthrough
Hack the Box Challenge: Sense Walkthrough
Hack the Box Challenge: Solid State Walkthrough
Hack the Box Challenge: Apocalyst Walkthrough
Hack the Box Challenge: Mirai Walkthrough
Hack the Box Challenge: Grandpa Walkthrough
Hack the Box Challenge: Blue Walkthrough
Hack the Box Challenge: Lame Walkthrough
Hack the Box Challenge: Blocky Walkthrough
Hack the W1R3S.inc VM (CTF Challenge)
Hack the Vulnupload VM (CTF Challenge)
Hack the DerpNStink VM (CTF Challenge)
Hack the Game of Thrones VM (CTF Challenge)
Hack the C0m80 VM (Boot2root Challenge)
Hack the Bsides London VM 2017(Boot2Root)
Hack the USV: 2017 (CTF Challenge)
Hack the Cyberry: 1 VM( Boot2Root Challenge)
Hack the Basic Penetration VM (Boot2Root Challenge)
Hack The Ether: EvilScience VM (CTF Challenge)
Hack the Depth VM (CTF Challenge)
Hack the G0rmint VM (CTF Challenge)
Hack the Covfefe VM (CTF Challenge)
Hack the Born2Root VM (CTF Challenge)
Hack the dina VM (CTF Challenge)
Hack the H.A.S.T.E. VM Challenge
Hack the RickdiculouslyEasy VM (CTF Challenge)
Hack the BTRSys1 VM (Boot2Root Challenge)
Hack the BTRSys: v2.1 VM (Boot2Root Challenge)
Hack the Bulldog VM (Boot2Root Challenge)
Hack the Lazysysadmin VM (CTF Challenge)
Hack the Zico2 VM (CTF Challenge)
Hack the Primer VM (CTF Challenge)
Hack the thewall VM (CTF Challenge)
Hack the IMF VM (CTF Challenge)
Hack the 6days VM (CTF Challenge)
Hack the 64base VM (CTF Challenge)
Hack the EW Skuzzy VM (CTF Challenge)
Hack the Analougepond VM (CTF Challenge)
Hack the Moria: 1.1 (CTF Challenge)
Hack the DonkeyDocker (CTF Challenge)
Hack the d0not5top VM (CTF Challenge)
Hack the Super Mario (CTF Challenge)
Hack the Defense Space VM (CTF Challenge)
Hack the billu: b0x VM (Boot2root Challenge)
Hack the Orcus VM CTF Challenge
Hack the Nightmare VM (CTF Challenge)
Hack the Bot challenge: Dexter (Boot2Root Challenge)
Hack the Fartknocker VM (CTF Challenge)
Hack the Pluck VM (CTF Challenge)
Hack the Sedna VM (CTF Challenge)
Hack the Quaoar VM (CTF Challenge)
Hack the Gibson VM (CTF Challenge)
Hack the Pipe VM (CTF Challenge)
Hack the USV VM (CTF Challenge)
Hack the Pentester Lab: from SQL injection to Shell II (Blind SQL Injection)
Hack the Pentester Lab: from SQL injection to Shell VM
Hack the Fortress VM (CTF Challenge)
Hack the Zorz VM (CTF Challenge)
Hack the Freshly VM (CTF Challenge)
Hack the Hackday Albania VM (CTF Challenge)
Hack the Necromancer VM (CTF Challenge)
Hack the Billy Madison VM (CTF Challenge)
Hack the Seattle VM (CTF Challenge)
Hack the SkyDog Con CTF 2016 – Catch Me If You Can VM
Hack Acid Reloaded VM (CTF Challenge)
Hack the Breach 2.1 VM (CTF Challenge)
Hack the Lord of the Root VM (CTF Challenge)
Hack the Acid VM (CTF Challenge)
Hack the SpyderSec VM (CTF Challenge)
Hack the VulnOS 2.0 VM (CTF Challenge)
Hack the VulnOS: 1 (CTF Challenge)
Hack the Fristileaks VM (CTF Challenge)
Hack the NullByte VM (CTF Challenge)
Hack the Minotaur VM (CTF Challenge)
Hack the TommyBoy VM (CTF Challenge)
Hack the Breach 1.0 VM (CTF Challenge)
Hack the SkyDog VM (CTF Challenge)
Hack the Milnet VM (CTF Challenge)
Hack the Kevgir VM (CTF Challenge)
Hack the Simple VM (CTF Challenge)
Hack the SickOS 1.2 VM (CTF Challenge)
Hack the SickOS 1.1 VM (CTF Challenge)
Hack the Sidney VM (CTF Challenge)
Hack the Stapler VM (CTF Challenge)
Hack the Droopy VM (CTF Challenge)
Hack the Mr. Robot VM (CTF Challenge)
Penetration Testing in PwnLab (CTF Challenge)
Hack the SecOS:1 (CTF Challenge)
Hack the Skytower (CTF Challenge)
Hack the Kioptrix 5 (CTF Challenge)
Hack The Kioptrix Level-1.3 (Boot2Root Challenge)
Hack the Kioptrix Level-1.2 (Boot2Root Challenge)
Hack The Kioptrix Level-1.1 (Boot2Root Challenge)
Hack the 21LTR: Scene 1 VM (Boot to Root)
Hack the Troll-1 VM (Boot to Root)
Hack the Hackademic-RTB2 (Boot2Root)
Hack the Hackademic-RTB1 VM (Boot to Root)
Hack the De-Ice S1.130 (Boot2Root Challenge)
Hack the De-ICE: S1.120 VM (Boot to Root)
Hack the pWnOS: 2.0 (Boot 2 Root Challenge)
Hack the pWnOS-1.0 (Boot To Root)
Hack the Holynix: v1 (Boot 2 Root Challenge)
Hack the LAMPSecurity: CTF8 (CTF Challenge)
Hack the LAMPSecurity: CTF 7 (CTF Challenge)
New York (CNN Business)Binance, a major cryptocurrency exchange, says hackers stole more than $40 million worth of bitcoin from its customers.
The Taiwan-based company, one of the world’s largest crypto exchanges, announced that it discovered a “large scale security breach” Tuesday. It said hackers stole 7,000 bitcoins in one transaction. One bitcoin trades at nearly $6,000.
Facebook makes a U-turn on Blockchain and cryptocurrency ads, CNBC reports. Hence, more crypto-oriented companies will be able to promote their products on the biggest social media network.
‘Facebook Coin’ Reportedly Coming in First Half of 2019
As reported by U.Today, Facebook relaxed is crypto ad ban back in June, but ICOs were still barred from the website. Despite this announcement, the social media giant continued to blackball the majority of crypto-related ads. The thing is, Facebook only readmitted the companies that already got the green light before the ban, but the majority of new submissions have been rejected (mostly for some obscure reasons).
Now, a wide range of crypto-related ads does not need to be pre-approved at all. It appears that only those ads that are promoting ICOs and other crypto projects will be vetted as usual by Facebook.
“While we will still require people to apply to run ads promoting cryptocurrency, starting today, we will narrow this policy to no longer require pre-approval for ads related to blockchain technology, industry news, education or events related to cryptocurrency,” the blog post read.
Back in October, Google also reversed its crypto ban for regulatory compliant exchanges after banning crypto ads along with a slew of other tech companies, such as LinkedIn and Snapchat.
Facebook had no choice but loosen its grip on crypto since it’s prepping to issue its own cryptocurrency that is supposed to become a major disruptor in the industry. Facebook’s foray into crypto is allegedly the reason why major institutions are becoming enthusiasticabout digital assets.
Source: U Today
We would’ve been talking about an extraordinarily low number of breached records this month if it hadn’t been for a string of incidents in India, another Facebook gaffe and a massive blunder in China, in which a series of companies exposed almost 600 million citizens’ CVs.
Still, April 2019 saw a not completely disastrous 1,334,488,724 breached records. That’s better than last month, bringing the annual total to 5.64 billion and reducing the monthly average to 1.46 billion.
Here’s the list in full:
Source: IT Governanace
Seminal fighting game “Mortal Kombat” was inducted into the World Video Game Hall of Fame at The Strong National Museum of Play in Rochester, New York on Thursday.
It joined “Super Mario Kart,” “Microsoft Solitaire,” and “Colossal Cave Adventure” as part of the 2019 class. The four inductees span multiple decades, countries of origin, and gaming platforms, but all have significantly influenced the video game industry, popular culture, and society in general, The Strong said.
Published by Midway Games in 1992, “Mortal Kombat” is one of the most recognizable fighting games around. Its hyper violent content led to major controversy, several court cases, and the creation of the Entertainment Software Ratings Board. Since then, it’s become one of the biggest media properties of all time, spawning nearly a dozen sequels, a television series, comics, feature films, and more.
Twelve finalists were announced for the 2019 World Video Game Hall of Fame class. They reportedly received thousands of nominations from more than 100 countries. To be eligible, the games must have longevity, geographical reach, and influence. They also need to reach cultural icon status.
Here is the full list:
Previous inductees include “Donkey Kong,” “Doom,” “Final Fantasy VII,” “The Legend of Zelda,” and the “The Oregon Trail.”
Source: Variety