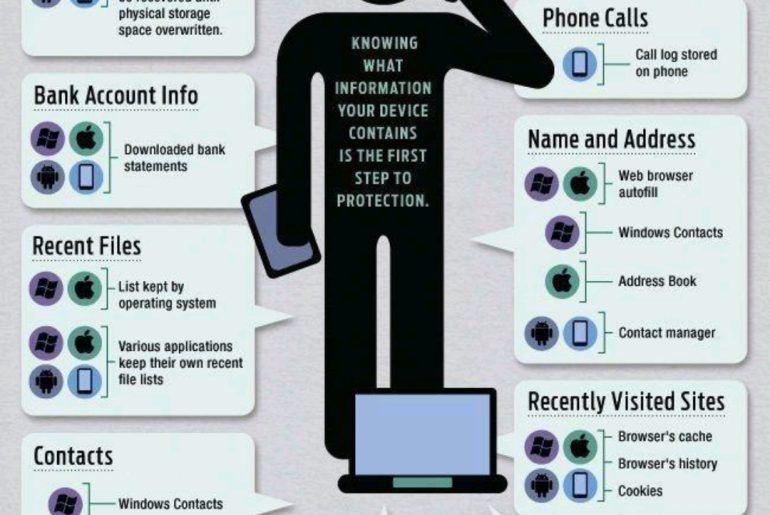
Source: CrowdStrike

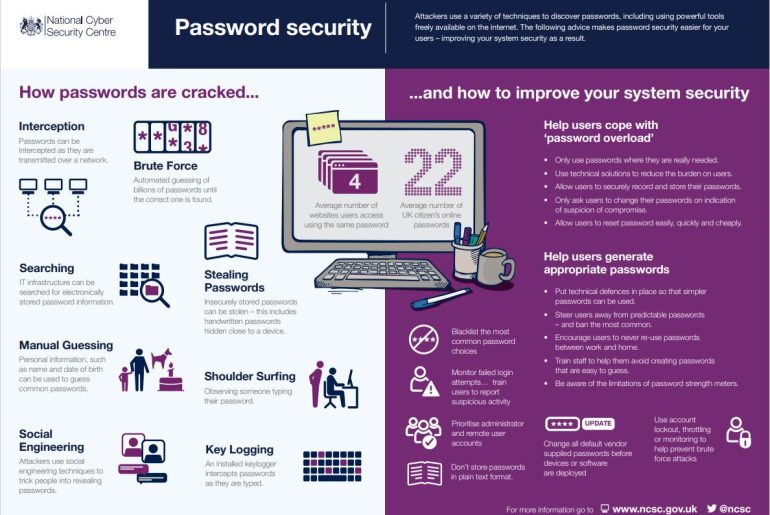
Source: NCSC
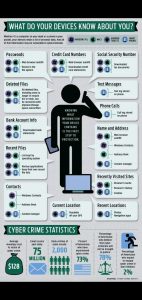
Source: Clario
bug bounty program is a deal offered by many websites, organizations and software developers by which individuals can receive recognition and compensation[1][2] for reporting bugs, especially those pertaining to security exploits and vulnerabilities.
These programs allow the developers to discover and resolve bugs before the general public is aware of them, preventing incidents of widespread abuse. Bug bounty programs have been implemented by a large number of organizations, including Mozilla,[3][4] Facebook,[5] Yahoo!,[6] Google,[7] Reddit,[8] Square,[9] Microsoft,[10][11] and the Internet bug bounty.[12]
Companies outside the technology industry, including traditionally conservative organizations like the United States Department of Defense, have started using bug bounty programs.[13] The Pentagon’s use of bug bounty programs is part of a posture shift that has seen several US Government Agencies reverse course from threatening white hat hackers with legal recourse to inviting them to participate as part of a comprehensive vulnerability disclosure framework or policy.[14]
Source: Wikipedia
A botnet [short for bot network] is a network of hijacked computers and devices infected with bot malware and remotely controlled by a hacker. The bot network is used to send spam and launch Distributed Denial of Service [DDoS] attacks, and may be rented out to other cybercriminals. Botnets can also exist without a command and control (C&C) server by using peer-to-peer [P2P] architecture and other management channels to transfer commands from one bot to another.
Because of the continuing development and broadening use of the internet of things (IoT), botnets created from connected devices have become more prominent. These are called IoT botnets, and they are largely similar in function to regular botnets.
Initially, botnet operators used IRC clients to deliver instructions and execute DDoS attacks. Much recent botnet operations were observed to have the ability to mine bitcoins, intercept any data in transit, send logs that contain sensitive user information to the botnet master, and consume the user’s machine resources. See infographic below:
Source: TrendMicro
The software development landscape changes constantly. New areas of specialization, technologies, and methodologies pop into existence every few months, forged by the relentless innovation of the software industry. With it, terms to describe specialized types of developers become part of the unofficial industry lingo and show up in job ads and corporate titles.
Before the existence of the internet, many of these specializations didn’t exist. The worldwide web has shifted most aspects of our lives, including revolutionizing the career paths of software engineers.
There isn’t an official industry glossary of terms. Understanding the skills that each type of developer needs to have is confusing to newcomers, and can be intimidating to non-technical people.
The cheat sheet below highlights the 3 major It Developer categories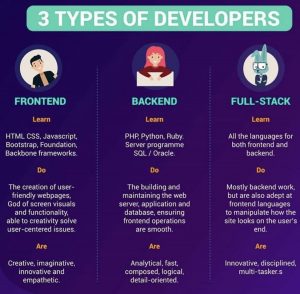
Other tiers similar to frontend, backend and full-stack developer include Middle-Tier Developer, which is a developer who writes non-UI code that runs in a browser and often talking to non-core code running on a server. In general, middle tier is the “plumbing” of a system. The term middle-tier developer is used to describe someone who is not specialized in the front-end or the back-end but can do a bit of both, without being a full stack developer. Only rarely engineers have this as a title, as it is more of a description of a skill set than a career path.
Until recently, end-to-end encryption (E2EE) was the sole domain of the tech savvy because of the complicated operations required to use it. However, recent technological advances have made end-to-end encryption much easier to use and more accessible. In this article, we will explain what is end-to-end encryption and what advantages it offers over regular encryption.
What is end-to-end encryption (E2EE)?
When you use E2EE to send an email or a message to someone, no one monitoring the network can see the content of your message — not hackers, not the government, and not even the company (e.g., ProtonMail) that facilitates your communication.
This differs from the encryption that most companies already use, which only protects the data in transit between your device and the company’s servers. For example, when you send and receive an email using a service that does not provide E2EE, such as Gmail or Hotmail, the company can access the content of your messages because they also hold the encryption keys. E2EE eliminates this possibility because the service provider does not actually possess the decryption key. Because of this, E2EE is much stronger than standard encryption.
How does end-to-end encryption work?
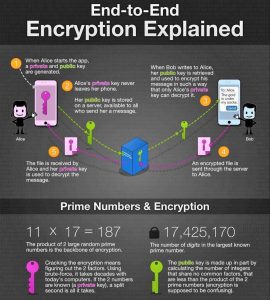
To understand how E2EE works, it helps to look at a diagram. In the example below, Bob wants to say hello to Alice in private. Alice has a public key and a private key, which are two mathematically related encryption keys. The public key can be shared with anyone, but only Alice has the private key.
First, Bob uses Alice’s public key to encrypt the message, turning “Hello Alice” into something called ciphertext — scrambled, seemingly random characters.
Bob sends this encrypted message over the public internet. Along the way, it may pass through multiple servers, including those belonging to the email service they’re using and to their internet service providers. Although those companies may try to read the message (or even share them with third parties), it is impossible for them to convert the ciphertext back into readable plaintext. Only Alice can do that with her private key when it lands in her inbox, as Alice is the only person that has access to her private key. When Alice wants to reply, she simply repeats the process, encrypting her message to Bob using Bob’s public key.
Advantages of end-to-end encryption services
There are several advantages of E2EE over the standard encryption that most services utilize:
- It keeps your data safe from hacks. E2EE means fewer parties have access to your unencrypted data. Even if hackers compromise the servers where your data is stored (e.g., the Yahoo mail hack), they cannot decrypt your data because they do not possess the decryption keys.
- It keeps your data private. If you use Gmail, Google can know every intimate detail you put in your emails, and it can save your emails even if you delete them. E2EE gives you control over who reads your messages.
- It’s good for democracy. Everyone has the right to privacy. E2EE protects free speech and shields persecuted activists, dissidents, and journalists from intimidation.
End-to-end encryption is the most secure way to communicate privately and securely online. By encrypting messages at both ends of a conversation, end-to-end encryption prevents anyone in the middle from reading private communications.
Source: Proton mail