Until recently, end-to-end encryption (E2EE) was the sole domain of the tech savvy because of the complicated operations required to use it. However, recent technological advances have made end-to-end encryption much easier to use and more accessible. In this article, we will explain what is end-to-end encryption and what advantages it offers over regular encryption.
What is end-to-end encryption (E2EE)?
When you use E2EE to send an email or a message to someone, no one monitoring the network can see the content of your message — not hackers, not the government, and not even the company (e.g., ProtonMail) that facilitates your communication.
This differs from the encryption that most companies already use, which only protects the data in transit between your device and the company’s servers. For example, when you send and receive an email using a service that does not provide E2EE, such as Gmail or Hotmail, the company can access the content of your messages because they also hold the encryption keys. E2EE eliminates this possibility because the service provider does not actually possess the decryption key. Because of this, E2EE is much stronger than standard encryption.
How does end-to-end encryption work?
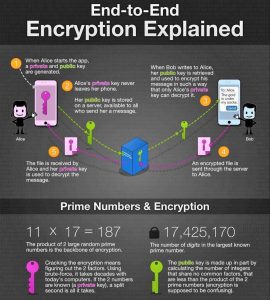
To understand how E2EE works, it helps to look at a diagram. In the example below, Bob wants to say hello to Alice in private. Alice has a public key and a private key, which are two mathematically related encryption keys. The public key can be shared with anyone, but only Alice has the private key.
First, Bob uses Alice’s public key to encrypt the message, turning “Hello Alice” into something called ciphertext — scrambled, seemingly random characters.

Bob sends this encrypted message over the public internet. Along the way, it may pass through multiple servers, including those belonging to the email service they’re using and to their internet service providers. Although those companies may try to read the message (or even share them with third parties), it is impossible for them to convert the ciphertext back into readable plaintext. Only Alice can do that with her private key when it lands in her inbox, as Alice is the only person that has access to her private key. When Alice wants to reply, she simply repeats the process, encrypting her message to Bob using Bob’s public key.
Advantages of end-to-end encryption services
There are several advantages of E2EE over the standard encryption that most services utilize:
- It keeps your data safe from hacks. E2EE means fewer parties have access to your unencrypted data. Even if hackers compromise the servers where your data is stored (e.g., the Yahoo mail hack), they cannot decrypt your data because they do not possess the decryption keys.
- It keeps your data private. If you use Gmail, Google can know every intimate detail you put in your emails, and it can save your emails even if you delete them. E2EE gives you control over who reads your messages.
- It’s good for democracy. Everyone has the right to privacy. E2EE protects free speech and shields persecuted activists, dissidents, and journalists from intimidation.
End-to-end encryption is the most secure way to communicate privately and securely online. By encrypting messages at both ends of a conversation, end-to-end encryption prevents anyone in the middle from reading private communications.
Source: Proton mail