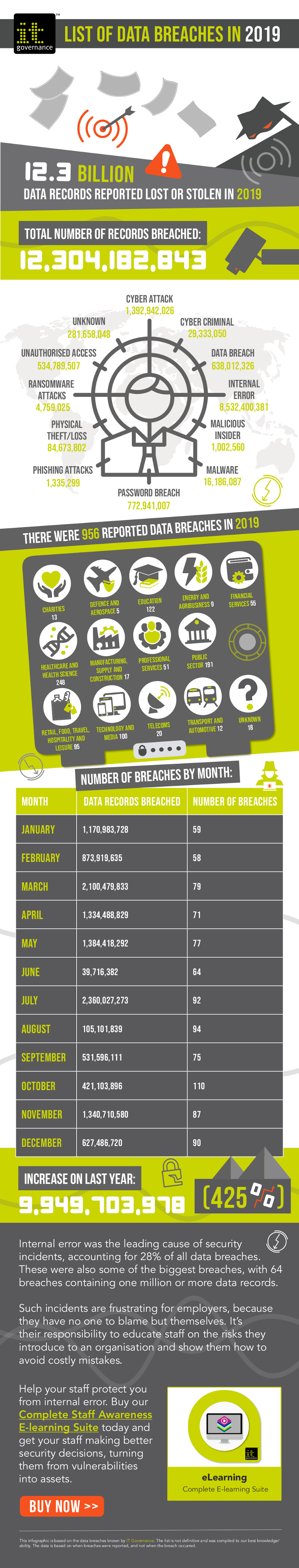
Covid-19 cases and cyberattacks following a similar curve – Thales
The study by Thales’s Cyber Threat Intelligence team shows that the pattern of malicious cyber activity matches the worldwide spread of Covid-19, with major attacks reported first in Asia, then in Central, Eastern and Western Europe.
In the midst of an unprecedented global health crisis, malicious actors are taking advantage of the situation to attack the information systems of companies, organizations, and individuals.
Hackers are using the pandemic as an opportunity to carry out targeted cyberattacks. Some of the new Android apps that track the propagation of the virus, for example, are infected with malware such as Trojan horses or ransomware.
There has also been an exponential increase in fraudulent or abusive activities online:
- Large numbers of domain names related to Covid-19 have been registered in recent weeks, more than 50% of which are thought to be part of “lure and decoy” operations.
- Large-scale spam campaigns using Covid-19 as a handle are attempting to spread ransomware, steal data or install banking malware.
- E-mail phishing campaigns are trying to get users to connect to fraudulent web pages offering downloads of comprised documents about Covid-19.
- Other e-mail campaigns are asking users to transfer money to sites claiming to be collecting charitable donations or to fake e-commerce sites offering personal protective equipment, for example. Initially, these attacks of opportunity were being carried out by cybercriminals, but a growing number of state-sponsored groups are now using the subject of Covid-19 to conduct various types of espionage.
Working from home: bigger risks for companies and organizations
The urgent introduction of large-scale teleworking or telecommuting is increasing cyber risks, not least because cyber attackers often try to comprise an organization’s information system by exploiting the following vulnerabilities:
- The use of personal devices for professional purposes (Shadow IT): employees working at home might use equipment or solutions that have not been approved by the company’s IT security specialists and are not under their control. This equipment can be a point of entry to critical data or the enterprise information system.
- Unauthorised installation of applications, software or tools that could be a security risk.
- Use of data storage solutions that offer inadequate security or have been deployed too quickly.
To help meet the IT security requirements of companies, organisations and their employees, Thales is now offering free access to two remote collaboration solutions — the Citadel professional chat and call app and the Cryptobox secure telework solutions — both of which are already widely used by French government agencies and major enterprise customers.
The remote connection to corporate applications and cloud services can also be at risk, especially when employee are working remotely. To help them connect securely, Thales also offers its SafeNet Trusted Access solution.
Risks are significantly higher than usual in these difficult times, so it’s more important than ever to protect your data, your networks and your information systems to avoid creating a cyber-crisis in addition to the health crisis we are already facing.
[embeddoc url=”https://itblogr.com/wp-content/uploads/2020/03/COVID-19-Cyber-Threat-Assesment.pdf” viewer=”google”]
Source: Thales