Researchers playing with Twinkly IoT lights found security weaknesses that allowed them to display custom lighting effects and to remotely turn off their Christmas brilliance. They estimate that about 20,000 devices are reachable over the internet.
The LEDs in Twinkly lights can be controlled individually. Exploiting inherent security weaknesses related to authentication and the communication of commands, the researchers were able to use the curtain of lights to play Snake, the game made so popular by Nokia phones in the late 1990s.
Users can manage their Twinkly smart decoration via a mobile app that sends unencrypted communication over the local network; this makes trivial analyzing the traffic from a man-in-the-middle position.
To talk to the lights, the app discovers them by running a UDP broadcast to port 5555 and receives in return an IP address and the name of the device.
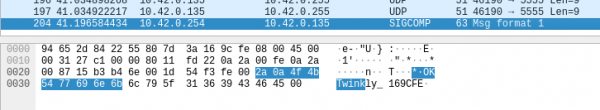
“Once the application knows the IP address of the lights, it authenticates with them, receives an authentication token and retrieves information about the device. The authentication process, although a good idea, is flawed,” said the researchers from MWR InfoSecurity, a company recently acquired by F-Secure.
After analyzing the hardware internals and the mobile app, the researchers had a clear view of how the entire communication and authentication process worked.
They found the calls to the API endpoints, the algorithms used for creating the authentication challenge-responses.
Another discovery relates to the firmware update process, which does not use signatures to check the authenticity of the files received; this allows installing an arbitrary firmware “to the device over the local network without any real authentication or authorization, making it straightforward to gain arbitrary code execution.”
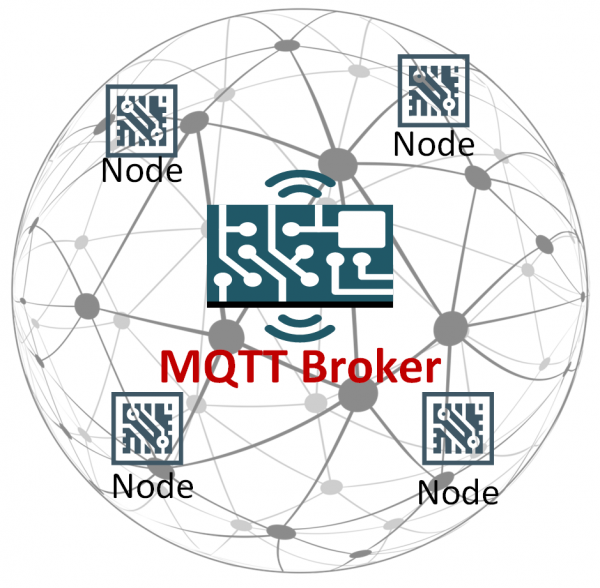
Hardcoded in the firmware is a username/password, used to connect to a private broker through the Message Queuing Telemetry Transport (MQTT) protocol for exchanging messages with remote IoT boards and sensors.
Seeking Reduced Risk?
See how Strategic Beta ETFs can help manage risk and seek to improve outcomes.
The MQTT protocol is not complex and it follows the publish/subscribe communication model, where the source and recipient of the message are oblivious of each other; when a publisher sends a message, it is received by all subscribers to that topic or class.
MQTT allows subscribing to a topic using wildcards using the symbol ‘#’ and doing so to the root means access to all topics and, implicitly, the information published by the lights.
“Monitoring the root for unique mac addresses we estimate there are almost 20,000 devices out there,” MWR Labs says.

Remote tampering with the lights is not difficult
Considering these security faults, it would be easy for an attacker on the network to intercept the communication between the Twinkly lights and the mobile app and use them to manipulate the LEDs into custom patterns or turn them off.
“As any MQTT node can publish to any topic, it is thus possible for anyone to issue commands to any set of lights and turn them off. We tested this remotely from AWS against the lights in the office and it worked perfectly,” MWR Labs experts note in a technical blog post.
To demonstrate remote management of the Twinkly lights across the world, the researchers turned to the DNS rebinding attack technique, known in the infosec industry for over a decade.
An attacker can use DNS rebinding to bypass the same-origin policy (SOP) in web browsers and turn them into a proxy for communicating with devices on the network. All the user would have to do for this to happen is access the wrong link.
MWR Labs created a malicious website specifically for this purpose. When the victim loads it, all the devices on the local network are enumerated. If Twinkly lights are available, they will be configured to show the message ‘Hack the Planet!’ as you can see in the video below.
The vulnerabilities found in Twinkly lights are the exact opposite for the IoT space. In this case, there is little damage an attacker can do by hacking the lights, but other targets may be more valuable, the researchers say.
Source: Bleeping Computer




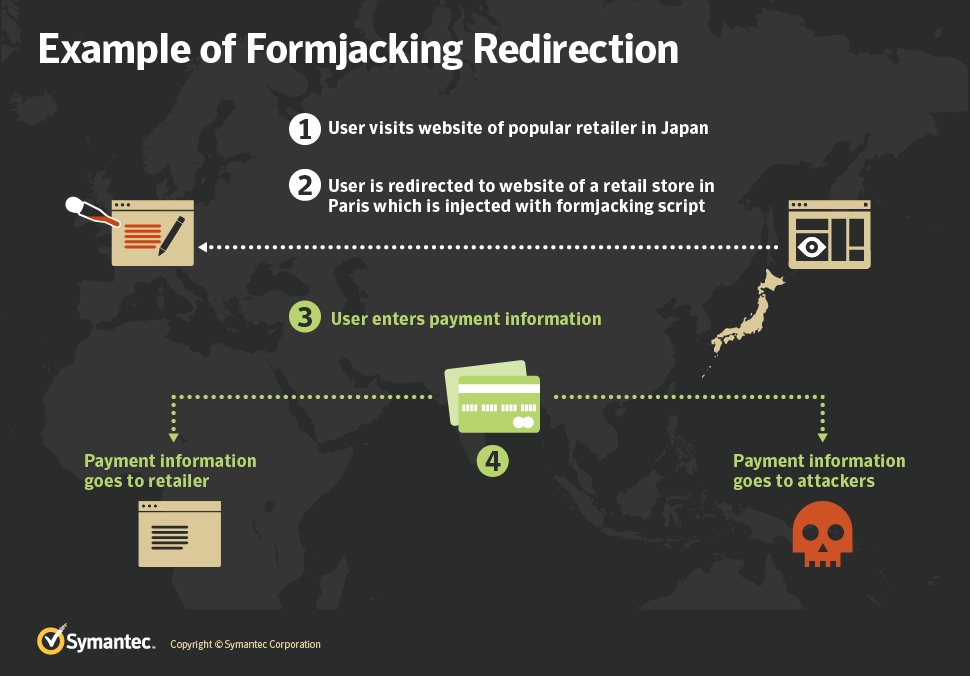 This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.
This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.